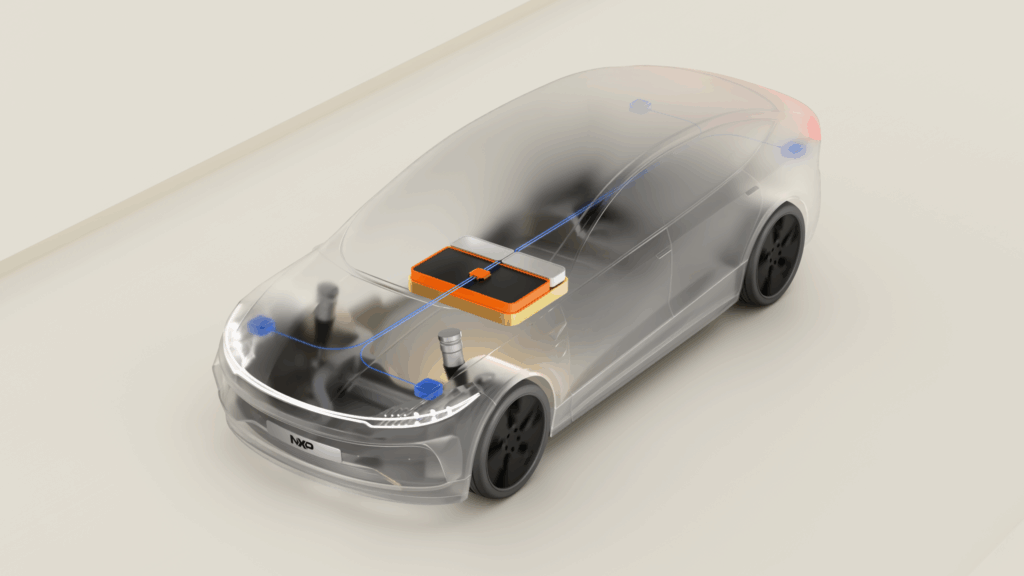
Machine-to-machine (M2M) communication in industrial and embedded environments demands a level of predictability that standard consumer Wi-Fi simply cannot provide. When deploying headless devices—ranging from autonomous mobile robots (AMRs) to remote telemetry gateways—engineers must navigate the specific physics and regulatory constraints of the 5 GHz band to ensure operational availability.
This guide examines the technical trade-offs of 5 GHz Wi-Fi, focusing on how to architect robust links for professional-grade embedded systems.
Understanding M2M Traffic Intent
In an embedded context, M2M usually involves devices exchanging data without human intervention. Success depends on categorizing traffic by its intent:
- Monitoring and Telemetry: Periodic messages where occasional packet loss is acceptable, but power efficiency is often paramount.
- Supervisory Control: Command-and-response cycles between a PLC and a gateway. Here, latency spikes can trigger system timeouts.
- Closed-Loop Control: High-stakes communication requiring bounded jitter. While Wi-Fi is rarely “deterministic” in the way a wired EtherCAT segment is, 5 GHz offers the spectrum hygiene necessary to approach those goals.
- Bulk Transfer: Firmware updates or high-resolution imaging. The challenge here is ensuring these bursts do not starve critical control traffic.
Why 5 GHz is the Professional Choice for M2M
While 2.4 GHz offers superior penetration through walls, the 5 GHz band has become the default for industrial deployments due to its capacity and reduced noise floor.
Capacity and Interference
5 GHz provides significantly more non-overlapping channels than the crowded 2.4 GHz band. In an industrial facility, this allows for much denser client environments and better frequency planning. Furthermore, 5 GHz is free from the interference of Bluetooth, Zigbee, and microwave ovens that plague the lower bands.
Range vs. Predictability
The shorter effective range of 5 GHz is often a deliberate design feature rather than a drawback. Smaller cells mean less co-channel interference and more efficient frequency reuse. However, engineers must account for “coverage sensitivity”—metal structures, machinery, and liquid tanks can cause SNR margins to collapse more abruptly than they do at lower frequencies.
Spectrum Management and Regulatory Hurdles
The 5 GHz band is a patchwork of sub-bands, each with its own EIRP (Effective Isotropic Radiated Power) limits and operational rules.
Channel Width: The Case for 20 MHz
While 80 MHz or 160 MHz channels offer impressive peak throughput, they are often a liability in M2M.
- 20 MHz: This is the gold standard for robust M2M. It provides the best range, the highest number of independent channels, and the most stable airtime.
- 40 MHz: A viable compromise for bulk data transfer if the RF environment is managed.
- DFS (Dynamic Frequency Selection): Many 5 GHz channels share spectrum with maritime and military radar. If an Access Point (AP) detects radar, it must vacate the channel immediately. For an AMR or a safety controller, this “DFS event” can cause a multi-second communication gap that must be handled at the application layer.
Link Budgets and Antennas
In embedded design, antenna placement often dictates success. Integration challenges include:
- Enclosure Effects: Placing an antenna inside a metal or carbon-fiber housing will severely detune the element.
- Polarization Diversity: For mobile assets like AGVs, using MIMO with varied antenna orientations helps maintain a link as the asset rotates through multipath-heavy environments.
Leveraging Wi-Fi 6 (802.11ax) in 5 GHz
The transition to Wi-Fi 6 brings features specifically designed to stabilize high-density M2M environments:
- OFDMA (Orthogonal Frequency Division Multiple Access): This allows an AP to talk to multiple low-bandwidth M2M sensors simultaneously in a single transmission window, reducing contention.
- Target Wake Time (TWT): Devices can negotiate exactly when they will wake up to communicate, significantly extending battery life for remote sensors and reducing unnecessary “chatter” on the medium.
- BSS Coloring: This helps devices ignore traffic from neighboring networks on the same channel, improving spatial reuse in dense factories.
Engineering for Reliability and Roaming
Since Wi-Fi is a contention-based medium, “reliability” is a function of architectural choices rather than a single setting.
The Roaming Challenge
For mobile M2M, roaming is frequently the weakest link. Most roaming decisions are client-driven, and embedded Wi-Fi drivers can be “sticky,” clinging to a weak AP even when a stronger one is nearby. Implementing 802.11k/v/r standards can assist, but engineers should define specific RSSI thresholds for roaming within the device firmware to ensure seamless transitions.
Redundancy Strategies
For mission-critical assets, consider a “Safe Mode.” If the 5 GHz link drops due to a DFS event or physical obstruction, the device should have enough local autonomy to reach a safe state. High-value systems often employ dual-radio clients—one locked to a non-DFS channel and another for high-speed data—to ensure a fallback path always exists.
Security and Lifecycle Management
Headless devices present unique security challenges because they lack a user interface for credential entry.
- Authentication: While WPA2-PSK is common, it is a liability at scale. WPA3-Enterprise using certificate-based authentication (EAP-TLS) is the professional standard, providing per-device identities that can be revoked without affecting the rest of the fleet.
- Provisioning: Modern workflows utilize BLE (Bluetooth Low Energy) or NFC for initial out-of-box commissioning, allowing a technician to securely pass Wi-Fi credentials to a headless node via a smartphone.
Final Design Recommendations
To achieve professional-grade M2M performance in the 5 GHz band, adhere to these core principles:
- Prioritize 20 MHz channels for all control and telemetry traffic.
- Conduct a site survey with the final mechanical enclosure to account for RF shadowing from machinery.
- Use WPA3 or EAP-TLS to move away from shared passwords.
- Implement application-layer retries and idempotent commands to handle the inevitable transient gaps inherent in wireless media.
By treating airtime as a finite resource and designing for the specific constraints of the 5 GHz spectrum, embedded engineers can deploy wireless systems that match the reliability of their wired counterparts.